Tech
Is Kubernetes Administrator Certification Good for You?
The CKA (Certified Kubernetes Administrator) curriculum ensures that CKAs have the essential knowledge, expertise, and competence to carry out the duties of a Kubernetes administrator. To deploy, scale, and maintain containerized apps automatically, Kubernetes Administrator serves best.
They founded CKA as having the potential to help grow the Kubernetes ecosystem, the Linux Foundation (LF) and Cloud Native Computing Foundation (CNCF). This performance-based test is a live, proctored, that evaluates a command line that runs Kubernetes to do several tasks.
CKA is specially designed for:
- Administrators of the system
- Certified DevOps Specialist
- Developers of software applications
Exam Description:
When a candidate schedules CKA Exam, it is available for one year after registration. A maximum of two tries are allowed after registering. The exam will last for two hours. 66 percent is required to pass. The validity of the CKA is three years. The exam costs $375, and one free retake is included.
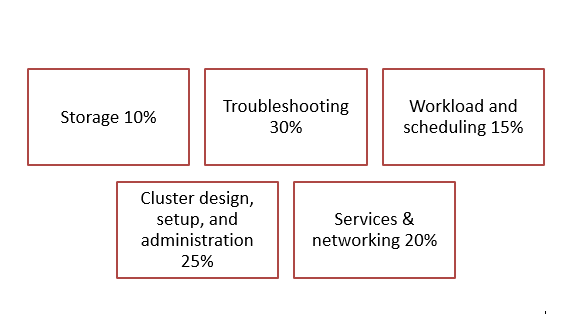
Exam CKA outline includes:
The exam covers all the essential topics which are highly trending. After attempting this course Candidate would be able to deal with all. The percentage shows the importance of that subject.
Prerequisites
This exam has no prerequisites. So it is the best choice to choose it for your best future.
Scheduling:
Scheduling for the CKA exam is easy. To see “My Portal,” the Candidate must first log in to the Linux Foundation’s LMS. To see which certificate exams or courses are currently active in your account, go to the “In Progress” tab. Keep in mind that First-time users will see an option labelled “Start Certification,” while those who have previously purchased will see “Resume,” respectively.
The Exam Preparation Checklist Items can be viewed by clicking the Start Certification (or Resume) button. Upon completion of these checklist items, the Candidate will be able to book an exam. After that, candidates will be given the option to pick a date and time that works best for them and a time zone.
The virtual computers must be prepared 24 hours before the exam, so the earliest available reservation date is the following day after the exam has started. Additionally, the scheduling calendar shows a 60-day window for the earliest possible date.
Advantages of CKA certificate:
Open source initiatives such as Kubernetes are experiencing a rise in popularity. There’s much demand for DevOps engineers who know how to administer Kubernetes clusters. A DevOps engineer’s compensation in Silicon Valley(a place in California famous for advanced technology companies) is currently 20% greater than that of a software engineer. DevOps engineers often earn between $140,000 and $200,000.
Since Kubernetes is used by a wide range of firms and organizations, getting CKA certification might help you gain a position within the industry.
Last Words:
The Linux Foundation’s Certified Kubernetes Administrator (CKA) certification is one of the most outstanding Kubernetes credentials. Dumpspedia is here to assist in getting a CKA certificate.
Such a Highly authentic and trustworthy Platform!
Kubernetes cluster setup and management is the focus of this course. It has been proven that a certified Kubernetes administrator By Dumpspedia can perform a basic installation as well as configure and manage production-grade Kubernetes clusters. By the time they advance and get more expertise, they know more about the basics of Kubernetes networking and memory, as well as encryption, debugging, API object primitives, and the lifetime of an application.
Best of Luck!
Tech
What Is PSA Software Used for in Project Management?


In the complex world of project management, staying on top of every task, resource, and deadline is a formidable challenge. This is where Professional Services Automation (PSA) software enters the scene, offering a comprehensive solution that covers project management, time tracking, billing, and beyond.
Leveraging such a tool can significantly improve efficiency and streamline processes within any project-oriented organization. Below, we delve into the depths of PSA’s multifaceted role in project management, providing insights into why it is becoming an indispensable tool for professionals in this field.
Understanding PSA Software in the Context of Project Management


PSA software has become essential in modern project management, providing tailored solutions for professional services firms. By streamlining operations, enhancing collaboration, and providing detailed project insights, PSA tools enable managers and teams to execute projects with precision and strategic insight.
As project management demands evolve, the importance of PSA software in achieving successful outcomes becomes more evident.
PSA software, short for Professional Services Automation, is a comprehensive suite of tools designed to streamline project management for professional service providers. It integrates various functionalities such as resource allocation, time tracking, and financial management to support the entire project lifecycle from start to finish.
PSA software offers a holistic view of projects, enabling managers to make informed decisions and optimize project components for success. By centralizing communication and project data in real time, PSA minimizes the risk of errors and miscommunication.
Its goal is to simplify project management processes, allowing teams to focus on delivering quality services rather than being overwhelmed by administrative tasks. So, what is PSA software? It’s the key to efficient and effective project management for service-based businesses.
Core Functions of PSA Software: Streamlining Operations
PSA software offers a suite of essential functions for optimizing project management. Key features include project planning, time tracking, expense management, invoicing, and resource management.
Project planning and scheduling allow managers to map timelines and assign tasks accurately, setting the foundation for project success. Time tracking and expense management ensure accurate recording of work hours and project expenses, maintaining budget control and maximizing billable hours.
Invoicing and billing processes are streamlined, ensuring accurate and timely billing, accelerating cash flow, and reducing errors.
Resource management facilitates the efficient allocation of human and material resources, optimizing productivity and work quality by selecting the right team members for tasks based on availability and skillsets.
How PSA Software Enhances Collaboration and Resource Management


Effective project management relies heavily on collaboration, and Professional Services Automation (PSA) software plays a vital role in enhancing this aspect.
By centralizing information and communication on a single platform, team members can collaborate seamlessly, share updates instantly, and access project details without delays. This synergy is crucial for maintaining a cohesive workflow.
PSA software also greatly improves resource management by providing a comprehensive view of available resources, enabling managers to assign them effectively based on project requirements and individual competencies. It helps in optimizing resource utilization, ensuring a balanced workload, and maximizing productivity.
PSA software facilitates better client interaction through client portals or integration capabilities, fostering transparent communication and project tracking from the client’s perspective. This transparency builds trust and enhances client satisfaction and retention rates.
Measuring Project Success with PSA Software’s Reporting Capabilities
Monitoring the health and progress of projects is crucial, and Professional Services Automation (PSA) software excels in providing robust reporting capabilities for this purpose. These systems offer customizable reports tracking key performance indicators, financial metrics, and project statuses, essential for measuring and communicating success to stakeholders.
PSA software’s real-time data analytics empower managers to swiftly identify trends and performance across multiple projects, facilitating the evaluation of methodologies and strategies for continual improvement.
Beyond mere numbers, PSA reporting captures the project narrative, highlighting achievements, challenges, and lessons learned. It serves as a platform for celebrating milestones and guiding future initiatives.
By consolidating vast project data into accessible reports, PSA software promotes transparency and accountability throughout the organization. This fosters a culture where every team member can understand their contributions to larger projects and organizational goals.
Altogether, PSA software has become essential in modern project management, providing tailored solutions for professional services firms. By streamlining operations, enhancing collaboration, and providing detailed project insights, PSA tools enable managers and teams to execute projects with precision and strategic insight.
As project management demands evolve, the importance of PSA software in achieving successful outcomes becomes more evident.
Tech
Harness the Emotion of Color in Web Design


In the field of web design Houston-based agencies, those specializing in “web design Houston” recognize the significance of color, beyond its aesthetic appeal. By leveraging color psychology they can craft websites that evoke feelings, influence user perceptions, and establish brand identities.
For instance, a soothing blue color scheme can foster trust on a financial services site whereas a website selling kids’ toys might benefit from the vibes of yellows and oranges.
The appropriate choice of colors not only enhances the attractiveness of a website but also subtly steers users towards desired actions like subscribing to a newsletter or making a purchase. Colors play a role in solidifying an online presence.
Through the use of colors that align with the brand’s message and target audience preferences web designers, in Houston can develop websites that make an impact.
- Evolutionary Influence: Throughout history, color has carried survival significance. Reddish hues might have signaled danger (like fire), while greens indicated safe, resource-rich environments. These associations are ingrained in our subconscious and continue to trigger emotional responses.
- Psychological Impact: Colors activate different parts of the brain. Warm colors (reds, oranges) tend to be stimulating and energetic, while cool colors (blues, greens) have a calming and relaxing effect. This can influence our mood, focus, and even heart rate.
- Cultural Meanings: Colors also hold symbolic value shaped by culture and experience. For instance, red might symbolize love in some cultures and danger in others. These learned associations can influence how we perceive brands, products, and even entire websites.
- Perception of Space and Size: Colors can manipulate our perception of size and space. Lighter colors tend to make an area feel more open and airy, while darker colors can create a sense of intimacy or closeness.
Color Psychology: The Fundamentals
The field of color psychology examines how the colors we perceive can impact our thoughts, emotions, and actions. It investigates the connections we make with shades whether they stem from reactions (such, as the vibrancy of red) or cultural meanings we’ve learned over time (like the purity associated with white).
Having a grasp of color psychology fundamentals provides designers with a toolbox. They can intentionally select colors to establish the atmosphere of a website and evoke feelings such, as calmness or excitement. Even alter perceptions of space by utilizing light and dark shades.
- The Color Wheel: A quick recap of primary, secondary, and tertiary colors.
- Warm vs. Cool: Emotional associations of warm (red, orange, yellow) and cool (blue, green, purple) colors.
- Individual Color Meanings: Delve into the common symbolism of colors in Western culture (e.g., red – passion/danger, blue – trust, green – growth).
Crafting Harmonious Color Palettes: A Systematic Approach
Creating color palettes involves a mix of knowledge and gut feeling. Begin by grasping the color schemes; use colors (opposites, on the color wheel) for a lively look analogous colors (adjacent hues) for a cohesive feel, or triadic colors (three equally spaced hues) for a well-rounded vibe.
Online tools can be super helpful in crafting palettes and experimenting with combinations. However, it’s crucial not to overwhelm users. Aim for a blend of colors that work well together striking the balance of contrast, for readability and accessibility.
Think about your brand image and the message you want to convey through your website when choosing colors. A curated color palette forms the foundation of a coherent and captivating web design services.
Color plays a role, in web design going beyond just the way it looks. By considering the psychological impact of color choices designers can evoke emotions direct users around a website strengthen brand recognition and create a memorable user experience.
A thought-out color scheme should align with the purpose of the website – using soothing colors for a healthcare site and lively shades for a kid’s brand – helping websites stand out in an online world.
Utilizing colors effectively can elevate a website from being visually attractive to being an instrument that influences user behavior positively and leaves a lasting impact.
- Emotional Impact: Color directly taps into our emotions, influencing how users feel as they interact with your website. Warm colors excite, cool colors calm, and the right combinations evoke specific feelings associated with your brand.
- Guiding the User: Strategic color use draws attention, creates emphasis, and improves usability. Contrasting colors make buttons pop, helping guide users towards your desired actions.
- Branding and Messaging: Your color palette becomes a core part of your brand identity. Users develop immediate associations, whether that’s the calming trustworthiness of a doctor’s office website or the playful energy of an online toy store.
- Standing Out: In a sea of websites, a well-designed color scheme makes you memorable. It separates you from competitors and creates a lasting impression that resonates with your target audience.
Tech
Taming the Current: Understanding and Preventing Electrical Overload


An electrical overload occurs when too much current is drawn through an electrical circuit, potentially leading to hazardous outcomes like fires or equipment damage. While both homes and businesses are at risk, industrial facilities with dense electrical infrastructure face some of the greatest overload hazards.
Think of electricity as water flowing through a hose. If you turn up the valve too high, the hose’s capacity will be exceeded, and you’ll either get leaks, pipe bursts, or damage from the excess pressure. Similar consequences happen when electrical current exceeds circuit capacities.
While momentary overloads may just trip a breaker, prolonged excessive current draws can lead to catastrophic equipment failures, fires, or other safety hazards. Industrial facilities are especially vulnerable due to their demands for dense electrical infrastructure.
Causes of Electrical Overloads
Several factors can contribute to electrical overloads:
- Circuit Overloading: This happens when too many devices are plugged into one circuit at a time. Even if those devices aren’t being actively used, their idle power draws accumulate to overload the circuit. Daisey-chained power strips liberally loaded with devices are a common overload culprit.
- Faulty Equipment: Malfunctioning appliances, machinery, or wiring along a circuit can also directly contribute to overloads. Examples are electrical shorts, corroded connections, old wiring unable to handle modern appliance loads, or devices drawing higher idle currents than normal. Damaged insulation and exposed wires also pose risks.
- Ground Faults: Also referred to as leakage current, ground faults occur when electricity strays or leaks from its intended path and instead flows into the grounding system. Although grounding systems are designed to handle some leakage, excessive ground faults can lead to overloads.
- Power Surges: From lightning strikes, damaged transformers, faulty generators, and similar causes, power surges slam electrical systems with sudden bursts of excess current. Without adequate protection, this abnormal influx readily overloads circuits.
- Simultaneous High Demand: At certain times, multiple pieces of equipment along a circuit could simultaneously start drawing higher loads, cumulatively exceeding that circuit’s capacity even if those devices typically don’t pose issues independently. Think of an industrial motor, air compressor, and conveyor belt system all powering up at once.
Consequences of Electrical Overloads
Electrical overloads create substantial safety risks and can cause extensive equipment damage. Here are some common consequences posed by electrical overloads:
Tripped Circuit Breakers
Circuit breakers are designed to trip and cut power as an early-response safety mechanism against sustained overloads. While the breaker trip protects downstream equipment, it also disrupts device functionality until the breaker is reset. Tripped breakers directly impact productivity in facilities that rely on constant electrical machinery uptime for operations.
Electrical Fires
Overheating wires and connections pose serious fire hazards, especially in industrial settings where flammable materials or dust accumulation could be present nearby. According to National Fire Protection Association estimates, electrical overloads account for around 30,000 fires per year just within industrial facilities.
Damaged Equipment
Beyond fire risks, sustained electrical overloads can simply fry electrical components involved in the overloaded circuit. Everything from motors, transformers, conductors, insulators, and more is at risk of heat degradation/mechanical stresses. The costs of replacing damaged electrical infrastructure can be substantial.
Power Outages
If overload conditions persist long enough before a protective breaker trips, the immediate equipment could sustain damage, causing a power outage further down the circuit. In drastic cases, the overload itself could theoretically trip the main breaker/fuse, cutting power to large sections of your facility. Loss of power triggers even more costly productivity impacts and safety risks for staff.
Preventing Electrical Overloads
Facility managers overseeing large electrical loads have several options available to prevent hazardous overloads proactively:
- Identify Circuit Capacity: Maintaining updated electrical drawings with load calculations for each circuit is invaluable. These help identify under-capacity circuits at risk of overload, especially when adding new equipment. Periodic infrared scans also help monitor heating issues along wires.
- Practice Smart Plugging: Encourage staff to be mindful of available outlets and avoid daisy-chaining surge protectors to prevent overloading circuits. Strategically distribute equipment across available circuits.
- Upgrade Outdated Wiring: If older electrical infrastructure lacks the capacity to support modern power demands, upgrades may be warranted to bring things up to code and safely add capacity margin.
- Invest in Surge Protectors: Commercial surge protectors help absorb anomalous power surges at key equipment or service panel locations, preventing overloads. They regulate voltage levels when abnormal spikes occur.
- Schedule Electrical Inspections: While building codes require routine inspections to uncover any overlooked risks like damaged wires or faulty equipment that could prompt overloads, even more frequent proactive inspections are worthwhile for aging electrical systems. Thermal imaging and breaker testing are example inspection focus areas.
- Unplug Unused Appliances: Remind staff to unplug seldom-used devices and equipment rather than leaving them plugged in indefinitely. All those idle current draws accumulate gradually, overloading circuits.
- Use the Right Size Fuses/Circuit Breakers: When replacing aged fuses or circuit breakers, ensure new components are properly rated for the intended equipment’s power demands with some extra capacity margin built in. Undersized components pose overload risks.
The Role of Metal-Clad Switchgear in Overload Protection
For handling large electrical current capacities across industrial facilities while guarding against overloads, metal-clad switchgears offer robust and safer power control solutions:
- High interrupting capacity: Designed to withstand short circuit currents up to 200kA, metal-clad switchgear can safely isolate and redirect excessive overload currents away from vulnerable equipment, better avoiding hazards.
- Operator safety: Unlike open busbar switchgear designs, metal-enclosed switchgear incorporates grounded metal barriers around current-carrying components, greatly reducing electric shock risks for staff during switchgear operation or maintenance. Doors with safety interlocks also prevent opening while energized.
- Modular construction: With individual cubicles for various switchgear functions like circuit breakers or instrument transformers, failed components are easier to isolate and replace without affecting adjacent equipment availability. This supports shorter downtimes. The modular designs also help simplify future expansion needs.
Proper metal-clad switchgears that provides a high level of protection at industrial sites safely and efficiently manages immense power flows. Protecting this vital equipment from excessive currents prevents costly outages and dangerous conditions. With a robust electrical backbone in place, operations can continue uninterrupted.
Conclusion
Electrical overloads pose substantial risks ranging from minor outages to fires and injuries. Targeted prevention is possible by understanding their causes – from circuit overloads to voltage imbalances.
Tactics like upgrading wiring, using surge protection, and ensuring properly sized breakers reduce overload likelihood. In industrial settings, investing in resilient metal-clad switchgears that provide a high level of protection manages extreme currents while insulating staff from harm.
With vigilance and safe infrastructure, electrical systems’ lifesaving protections will switch on the moment trouble arises.
-



 Captions3 years ago
Captions3 years ago341 Sexy Captions to Fire Up Your Instagram Pictures
-



 Captions3 years ago
Captions3 years ago311 Night Out Captions for Instagram and Your Crazy Night
-



 Captions3 years ago
Captions3 years ago245 Saree Captions for Instagram to Boost Your Selfies in Saree
-



 Captions3 years ago
Captions3 years ago256 Best Ethnic Wear Captions for Instagram on Traditional Dress
-



 Captions3 years ago
Captions3 years ago230 Blurred Picture Captions for Instagram
-



 Captions3 years ago
Captions3 years ago275 Deep Captions for Instagram to Express Your Thoughts
-



 Quotes3 years ago
Quotes3 years ago222 Nail Captions for Instagram to Showcase Your Fresh Manicure
-



 Captions3 years ago
Captions3 years ago211 Laughing Captions for Instagram | Laughter Is the Best Medicine







